Made possible by generous funding from

Phishing Scams. Crooks Pretending to be Trustworthy
You wouldn’t give your credit card number or banking password to a stranger who calls you out of the blue. But if a scammer can con you into believing they are a bank investigator trying to stop a hack on your account, then you might divulge confidential information. If, as an employee, you receive an email that appears to come from a manager in the IT (Information Technology) department directing you to click on a link and reset your password, you might follow the fraudulent link in the email and give your credentials to a cybercriminal. These frauds have something in common. They appear to come from a person or company that they are, in fact, not. Pretending to be someone while committing fraud is called phishing.
Phishing attacks come in all forms, including emails, text messages, and robocalls. Phishing ploys are designed to trick victims into revealing passwords, account numbers, or other personal information by leading them to a dangerous website or connecting them with a scammer on the phone. Typical phishing ploys use social engineering to instill fear or create a sense of urgency. Phishing scams are prevalent because they are easy to use and very effective.
Phishing scams often start with text messages
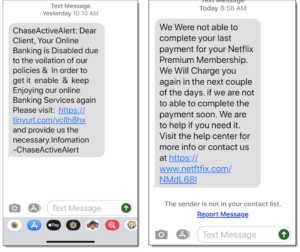
Here are two text messages that purport to come from legitimate businesses. The links go to fraudulent sites that will ask for passwords and account information. Notice the misspelling of “netftfix.com” in the link.
Businesses are prime targets for phishing
Hacking business databases can be a time-consuming process, and hacking requires coding skills. It’s much easier to trick an employee into divulging passwords or spilling the contents of databases. Scammers call or send emails pretending to be an executive, a manager, or someone in tech support or human resources. Recently, an organized phishing attack successfully compromised high-profile Twitter accounts, including celebrities and even a former president.
How to recognize phishing
Typical phishing ploys you’ll encounter use social engineering and purport to come from legitimate companies. Typical phishing examples include:
- Messages that appear to come from subscription services (like Netflix) or utility companies, claiming a recent payment failed due to a credit card issue. The links in the message lead to fake websites that send your log-in credentials directly to the scammer.
- A message that appears to come from your bank claiming suspicious activity is occurring on your bank account. These often come as robocalls or text messages. Again, the purpose is to trick you into revealing your login information to a cybercriminal.
- A message asking for confirmation of a purchase that you didn’t make.
- Messages that claim you have won a prize or contest. Sometimes these frauds ask for you to deposit money in order to collect your winnings.
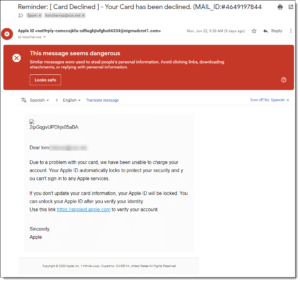
This email purports to be from Apple and uses fear and urgency (social engineering) to urge me to click a link that opens a page that looks official, but actually sends my Apple log in credentials to a scammer. Notice it was flagged by Gmail as a scam. A quick check of the sender’s address shows it was not sent from apple.com.
Other types of phishing scams
- Spear phishing. A spear-phishing attack targets a specific individual or company.
- Whaling. A whaling attack goes after a big fish, like a high-placed executive, politician, or celebrity.
- Catfishing (catphishing). Catfishing uses a romantic relationship to perpetrate fraud.
- Smishing (SMS phishing). Smishing refers to using text messages to commit fraud.
Websites can look official even when they are completely fake
As we discuss in the website address (URL) module, fraudulent websites can look official. A link you receive in a phishing email or text message can lead to a website that looks legitimate right down to the logo and the login box for your username and password. A fraudulent website will send your credentials, or any other information you enter, directly to the scammer.