If someone hacked into your Facebook, email or online banking account, would you know it?
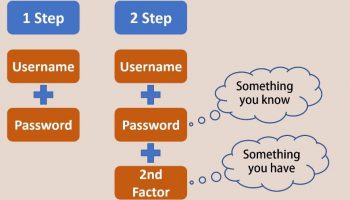 When Two Factor Authentication (2FA) is enabled it adds a second barrier for hackers who might be trying to access your accounts. This means that even if someone discovers your password, they can’t get into your account unless they have physical possession of your cell phone. This is the two-factor part: something you know (your password) and something you have in your possession (your cell phone).
When Two Factor Authentication (2FA) is enabled it adds a second barrier for hackers who might be trying to access your accounts. This means that even if someone discovers your password, they can’t get into your account unless they have physical possession of your cell phone. This is the two-factor part: something you know (your password) and something you have in your possession (your cell phone).
It is vitally important to choose strong passwords. Adding 2FA provides more peace of mind because it uses two factors to complete a password change. 2FA works by sending you a text message confirming that you have indeed requested to change your password.
Here is an example: Each morning you check Gmail, Facebook and your bank account balance on your computer before you leave home to meet up with friends, volunteer and then pick up some groceries to return home for dinner. While you are out, you get a text message on your cell phone from Google providing a code necessary to complete a change to your account.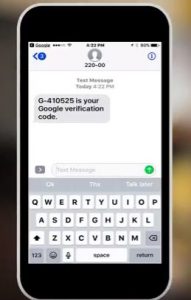
Since you have not requested to change your password on your Google/Gmail account, this text message is an alert that someone is attempting to change your Google password and that someone isn’t you. Disregard the code in this message and change your Google password as soon as you are able to.
Once you are back at home and ready to change the Google password, you will need your cell phone with you. Change the password as you normally would. Once you set up 2FA, your device will receive a new unique code that is generated when you really did change your password.
2FA is essential to protect your email account. If someone gains access to your email, it can be used to reset other passwords and access your other accounts.
2FA is just one helpful strategy to keep you a step ahead of cybercriminals. Check out the Oasis Connections YouTube Channel to learn how to set up 2FA, avoid phishing, use secure https sites and create strong passwords.