It all starts with an email, often from someone you know
The phishing attack starts with an email, often someone you know who has been hacked. The attacker is using the victim’s contact list to find more people to prey upon. Once you click on an included link or image, instead of a preview of the image, your browser opens with a Google sign in page. It looks like a real Google sign in page, only it isn’t.
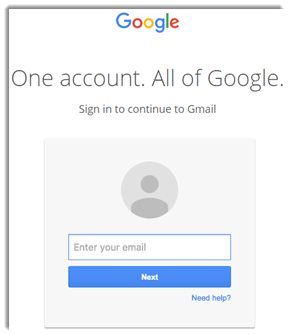
The address in the URL box isn’t an address, it is malicious code
This is what the URL box looks like. It has official looking text, and the “google.com” portion. But it isn’t a web address, it is malicious code that submits your email and password to the hackers behind the scam.
![]()
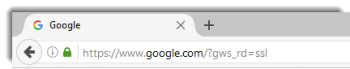
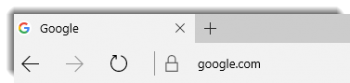
Look for the lock symbol and a properly formed URL
This is what a real Google web page URL looks like. All major browsers will have a lock icon, all except Microsoft’s Edge will show you the “https://” portion of the URL.
Firefox browser
Edge browser
Internet Explorer
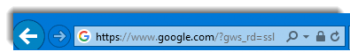
Chrome browser
How do you protect yourself?
Always be at least a bit suspicious of anything sent via email. Enable 2-factor authentication that uses a second validation, like a text message to your phone or a security key, in addition to your password.
Hackers have become more sophisticated and are using tactics, one of which is appearing to be someone you know, to try to gain your trust. These tactics are referred to as social engineering. For more details about this phishing scheme, read this post from Wordfence.